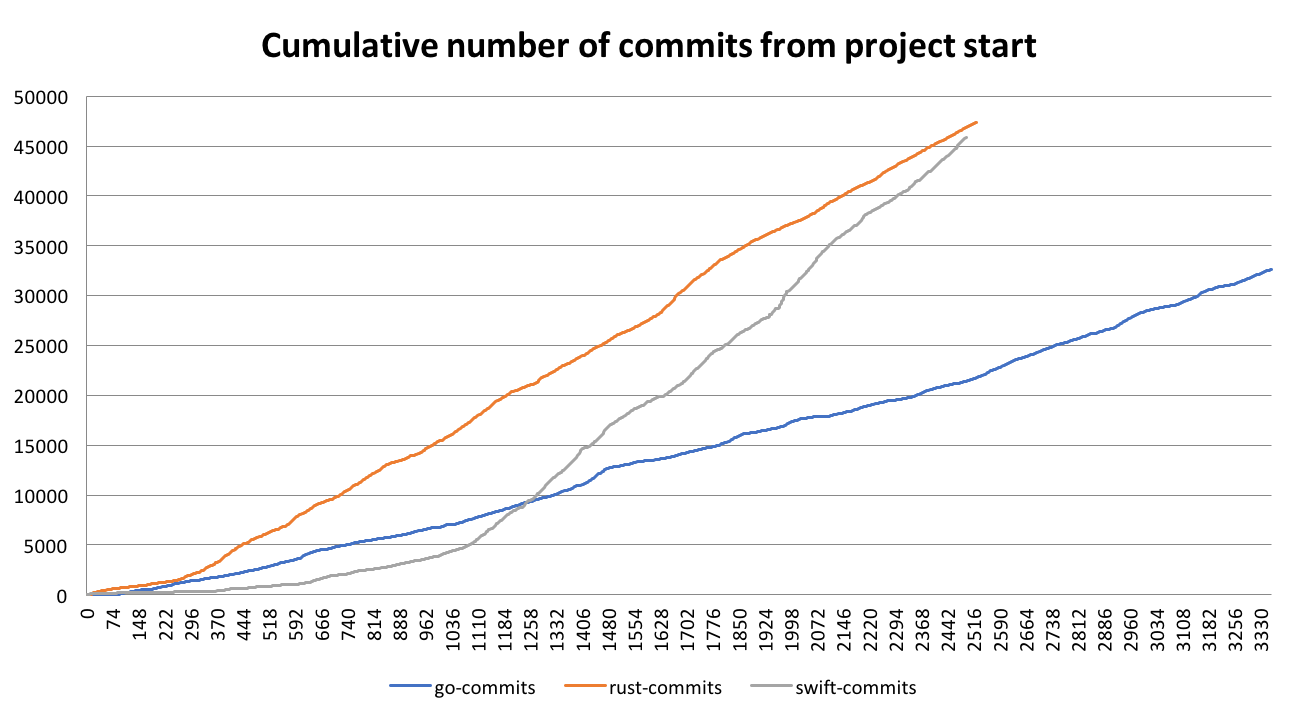
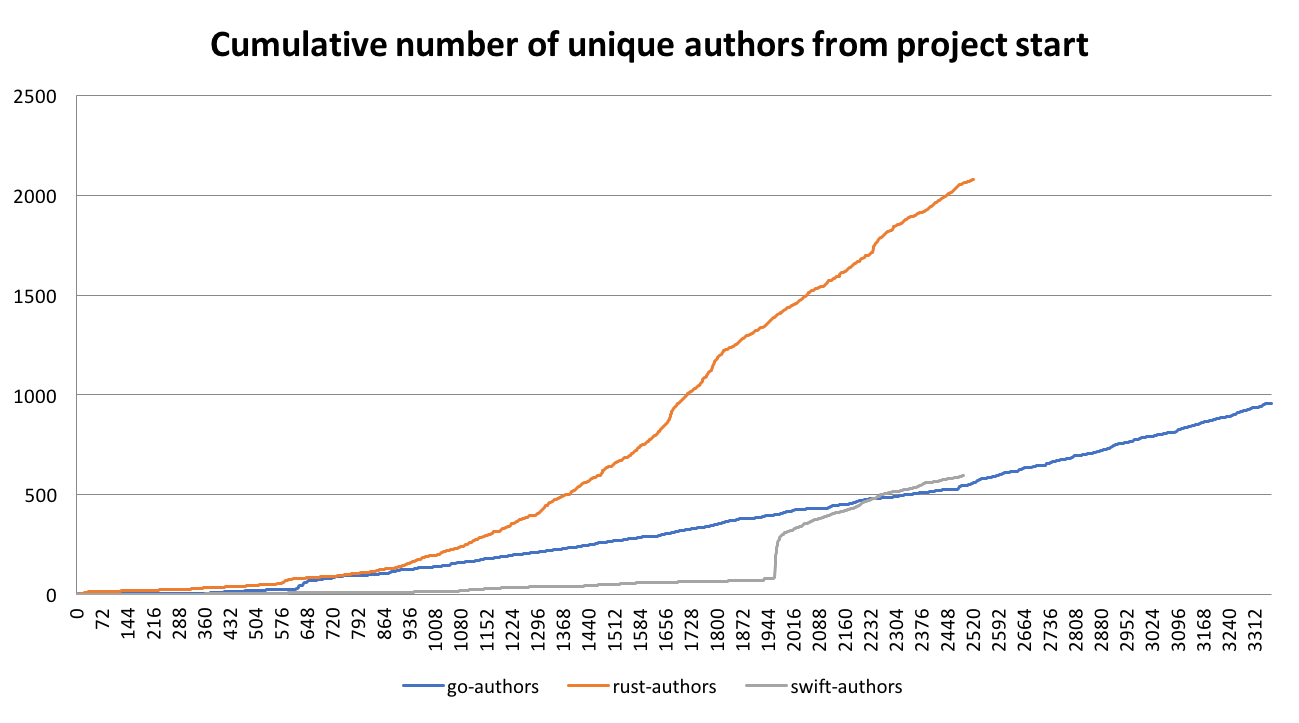
Since leaving my job at the end of August, I figured I would try to write up a report of most of the open source stuff I worked on (see previous month). Turns out writing these is a lot of work, so it took me a while to write up October's activity -- I ultimately wrote this with the help of some tooling I wrote.
rustls
rustls is a pure Rust implementation of the TLS protocol.
Here are some things I worked on:
- I migrated both tokio-rustls and rustls-native-certs to the new PEM API in rustls-pki-types (as discussed last month), cutting down on dependencies.
- I implemented the Error trait for the new pem::Error type in rustls-pki-types, which we had missed in the PR implementing PEM decoding.
- As I tried to switch instant-epp (see below) to the rustls-platform-verifier, I had to remind myself of how the high-level rustls-platform-verifier worked and found it non-trivial to incorporate into the instant-epp RustlsConnector. I decided to improve the API by exposing a couple of extension traits, which needed some additional rustls API (adding API while net removing code!).
- Reworked the rustls-native-certs README to clarify that most users should use rustls-platform-verifier instead, as an alternative to an earlier PR which made more cautious changes, and linked to the deployment considerations.
- I addressed an issue report about excessive logging in rustls by refining when we log warning alerts.
Joe and Daniel did more performance work:
- Improve receive performance
- server: default send_tls13_tickets 4 -> 2
- Faster TLS1.3 server resumption
- bench: match default BoringSSL/OpenSSL ticket count
- Make ciphersuite enum smaller
This culminated in a post on how rustls outperforms OpenSSL and BoringSSL.
There was some discussion on a better interface to setting the certificate verifier for an entire process, potentially by mimicking the crypto provider API.
Finally, initial support for RFC 7250 raw public keys (which is helpful especially in P2P scenarios) was released as part of 0.23.16.
Hickory DNS
Hickory DNS is a project to build a comprehensive suite of Rust libraries to build DNS services on top of. Because the project is nearing a (fairly large) feature release, I've been trying to make a number of improvements to the project, cleaning up the API and moving code around to reduce complexity.
- I removed the synchronous client API, which was a thin, not very well maintained wrapper around the larger, more capable async API. This entailed porting some tests and also removing the synchronous resolver API.
- I started looking at the DNSSEC cryptography API to figure out what needed to be done to both support ring as a full-fledged replacement for OpenSSL and add support for the ring-like aws-lc-rs provider. The DNSSEC API wasn't very well-designed, so this took quite some efforts. I started by looking at the KeyPair type which had a lot of functionality attached to it, and cleaned it up by moving code out of it and clarifying private/public key responsibilities.
- Improved CI cycle times by avoiding unnecessary release builds.
- Made a number of generic code quality/API improvements, like simplifying socket address literals, moving StoreConfig to bin crate, making error modules private, switching to using doc_auto_cfg, cleaning up rustdoc warnings, and replacing TryParseIp trait with IntoName::to_ip().
- Simplified rustls usage by leveraging the new PEM reading API.
Notable PRs I reviewed:
- Start propagating NX domain and no record found errors.
- Marcus addressed a very old request to enable blackholing DNS requests.
- Someone contributed an implementation of the CERT record type from RFC 4398 for storing certificates in the DNS (likely with some LLM help).
- David added configuration to avoid specific UDP ports on outbound traffic.
KumoMTA
I've been doing some consulting work for KumoMTA, a startup building a mail transfer agent (MTA) for enterprise senders. In October, I continued my work on SPF support, threading through the raw SPF implementation to the Lua-based configuration API and generalizing the DNS resolution API.
Quinn
Quinn is the most popular Rust implementation of the QUIC transport protocol.
I wasn't very active on Quinn in October, and only fixed a small bug in the datagram state management around dropping too large datagrams.
Fortunately, several other folks contributed interesting work:
- A Solana engineer contributed an optional alternative send stream scheduling strategy as well as work to reduce memory allocations.
- An Iroh engineer changed quinn-proto such that it can be used on the wasm32-unknown-unknown target.
- Someone cleaned up some edge cases in idle timeout negotiation.
- Someone added support for aws-lc-rs FIPS cryptography.
- A Mozilla engineer implemented faster UDP/IO on Apple platforms.
- Someone enabled support for Apple's visionOS and tvOS platforms.
tracing-opentelemetry
For lack of anyone else doing the work, I maintain the tracing-opentelemetry integration crate that allows the tracing project to work with the opentelemetry crates. The OpenTelemetry Rust SIG have been increasing the pace of semver-incompatible releases, but unfortunately missed some things.
- As such, I cleaned up their tonic code generation to use the right crate versions and bumped their MSRV to match the new dependencies.
- I wrote up a note in the tracing-opentelemetry README on version compatibility between the opentelemetry-* crates and tracing-opentelemetry.
- Reviewed the upgrade to opentelemetry 0.26.
- Reviewed a locking efficiency improvement.
- Reviewed optional attaching the level of exported spans.
bb8
bb8 is a full-featured async connection pool for Tokio. Apparently it's being used in PgCat, because an AWS engineer dropped by with some improvements:
- Notify one waiter per pending connection
- Track open requests to avoid creating unnecessary connections
- Reap expired connections on drop
(The latter two were ultimately merged as part of a roll-up PR that added some cleanup, and released with other accumulated fixes as 0.8.6.)
instant-epp
instant-epp implements the EPP protocol used for provisioning domains. It relies on instant-xml (see below) for getting the namespace-heavy EPP specs right. Although instant-epp does not see a lot of activity, a contributor popped up that contributed some changes. Apparently most EPP users fork their dependencies instead of contributing upstream -- or funding upstream development.
instant-xml
instant-xml is a serde alternative specifically focused on the XML data model, with pretty good support for XML namespaces (which is necessary for EPP). The same person who contributed changes to instant-epp also made some minor improvements in instant-xml to facilitate their development.
instant-acme
instant-acme is a RFC 8555 client for provisioning TLS certificates.
Reviewed a contributed PR to expose account IDs, which can be used in CAA records to restrict which account can request certificates.
gcp_auth
gcp_auth is a simple API for authenticating to Google Cloud Platform services. It supports both production and development environments, similar to official Google SDKs for other languages (though likely more limited in scope).
In October, someone contributed support for setting the audience in custom service account token providers, which had been asked for a few times.
chrono
chrono is one of the most popular date/time libraries in the Rust ecosystem. I took over maintenance because the previous maintainers didn't want to maintain it anymore, so I support the community by reviewing incoming pull requests.
This month, someone contributed support for OpenHarmony OS.
On sustainability
Since my last post, a few more companies started sponsoring my work, for which I am very grateful. For now, I'm still funding most of my open source activity from contract work, though I'm currently talking to some organizations that are looking to more directly fund open source work. Excited to see how that goes!
Many thanks to these sponsors (5 USD/month or more):
- syntaxfm
- getsentry
- denoland
- ctz
- astral-sh
- bdaehlie
- Quad9DNS
- thomaseizinger
- stepfunc
- tweedegolf
- codecov
- repi
- MJDSys
- mstange
- stackabletech
- dimlev
- Shnatsel
- eightseventhreethree
- malyn
- dconnolly
- paolobarbolini
- block